-
Stable levels
compared to voice fraud
-
4-5%
of global traffic is fraudulent, both in P2P and A2P traffic
-
Spam/Smishing attacks
are the biggest threat
-
Longer run rates for SMS attacks
compared to voice attacks
-
Up to 80%
of smishing attacks intercepted by BICS target EU citizens and carry EU CLIs
-
Source: BICS
SMS fraud


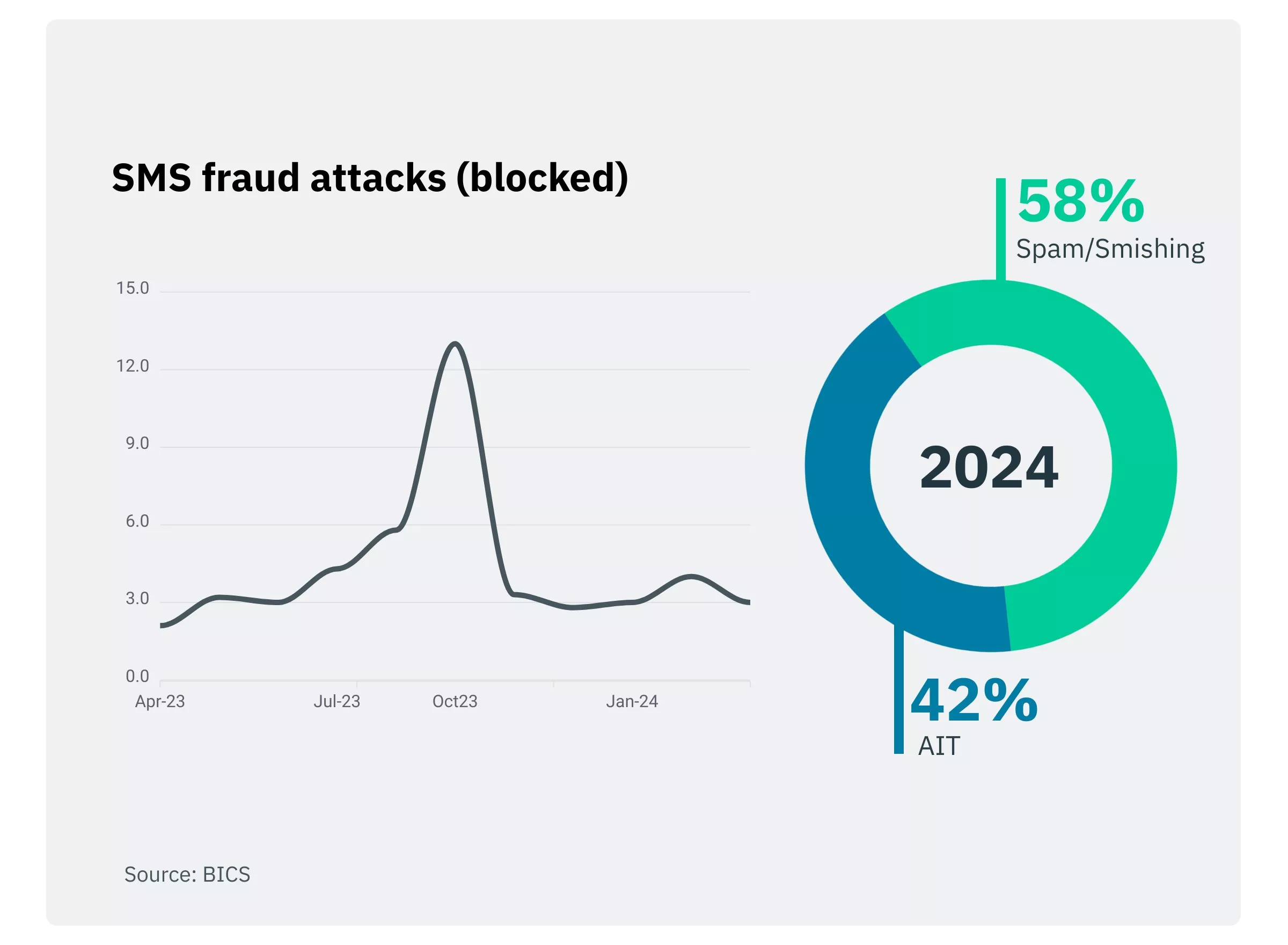
While SMS fraud is not showing the same sharp increase as voice fraud, there are still considerable volumes of it across both A2P and P2P channels around the world, with smishing levels being higher on P2P and AIT affected A2P channels more.
From a technical point of view, SMS fraud is more complicated to detect and prevent than voice fraud. This is in part because a single malicious number can target up to 100 end-users, so the surface attack is much larger than with voice fraud. Another reason is that it is a more recent form of fraud and there are less efficient tools available, and mobile network operators (MNOs) and enterprises are both less well equipped to stop it. As a result, it should still be an important concern for operators, especially considering that SMS attacks often have a longer run rate than voice-based fraud.

Smishing
The basic concept of smishing is the same as phishing calls: fraudsters use deception to trick recipients into providing personal information or clicking on malicious links. The only difference is the use of SMS as a medium.
Though smishing has been around for many years, fraudsters are constantly refining their techniques and using enterprise technology to increase their reach. Recently, they have begun using call centers as a hub for triggering smishing attacks and therefore successfully reaching a much wider range of victims than ever before. This means that it is no longer just end-users that are at risk, but enterprises and operators themselves, too.
The increase in volume is reflected in the numbers: BICS counted 345 million smishing messages in Europe between January 2023 and May 2024.
In 2023, a Chinese-speaking criminal group called Smishing Triad was identified. The group successfully impersonated a number of postal and delivery services, from the UK’s Royal Mail to USPS and the New Zealand Post. They used iMessage to send package-tracking scam messages and collect victims’ personal data. The group was also revealed to be operating a fraud-as-a-service network, selling “smishing kits” which allowed buyers to retrieve data from as many as 108,000 victims.

Artifically Inflated Traffic (AIT)
The Mobile Ecosystem Forum (MEF) defines two main types of Artificially Inflated Traffic (AIT). First, AIT can be used to defraud a business by creating bots which pretend to be users and send out one-time password verification (OTP) via the business’ messaging account to certain numbers controlled by the fraudster, who can block the artificial traffic when it hits the network node. The fraudster then makes a profit directly or indirectly from the messages while the business loses revenues.
The second AIT fraud type targets mobile network operators (MNOs) directly by sending repeated messages to virtual numbers controlled by cybercriminals to generate an outpayment. The fraudster makes a profit as the cost of sending the messages is lower than the outpayment.
The impact of AIT is now so severe that it is often cited as the biggest threat to A2P SMS monetization, surpassing grey routes or even smishing.

In 2023, the platform X (formerly known as Twitter) reported annual losses of $60 million due to AIT scams, with fake 2FA (two-factor authentication) messages being sent to the platform and then monetized through a revenue share scheme with malicious operators. The issue was so large that it prompted X to remove 2FA for non-subscribers.




