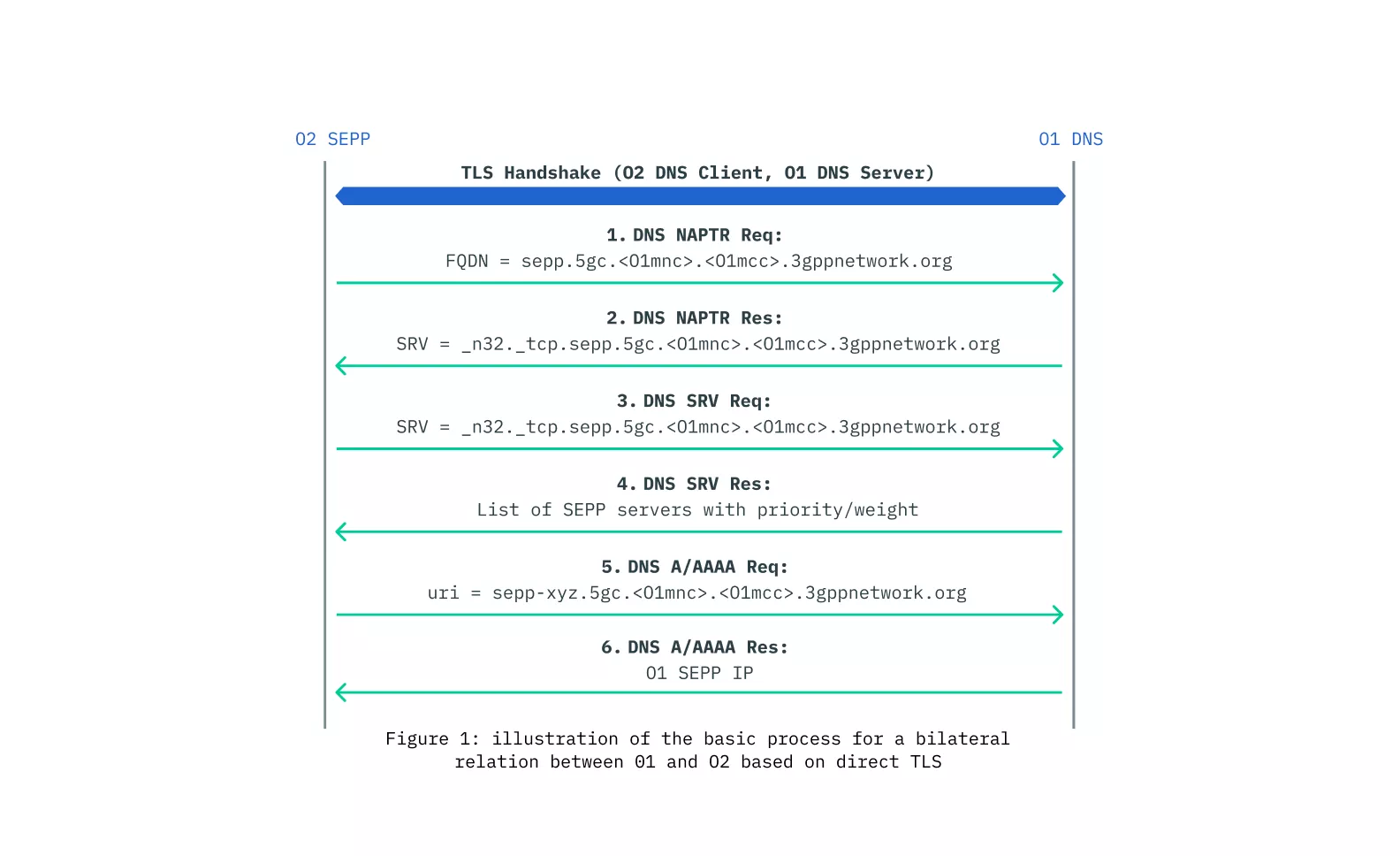
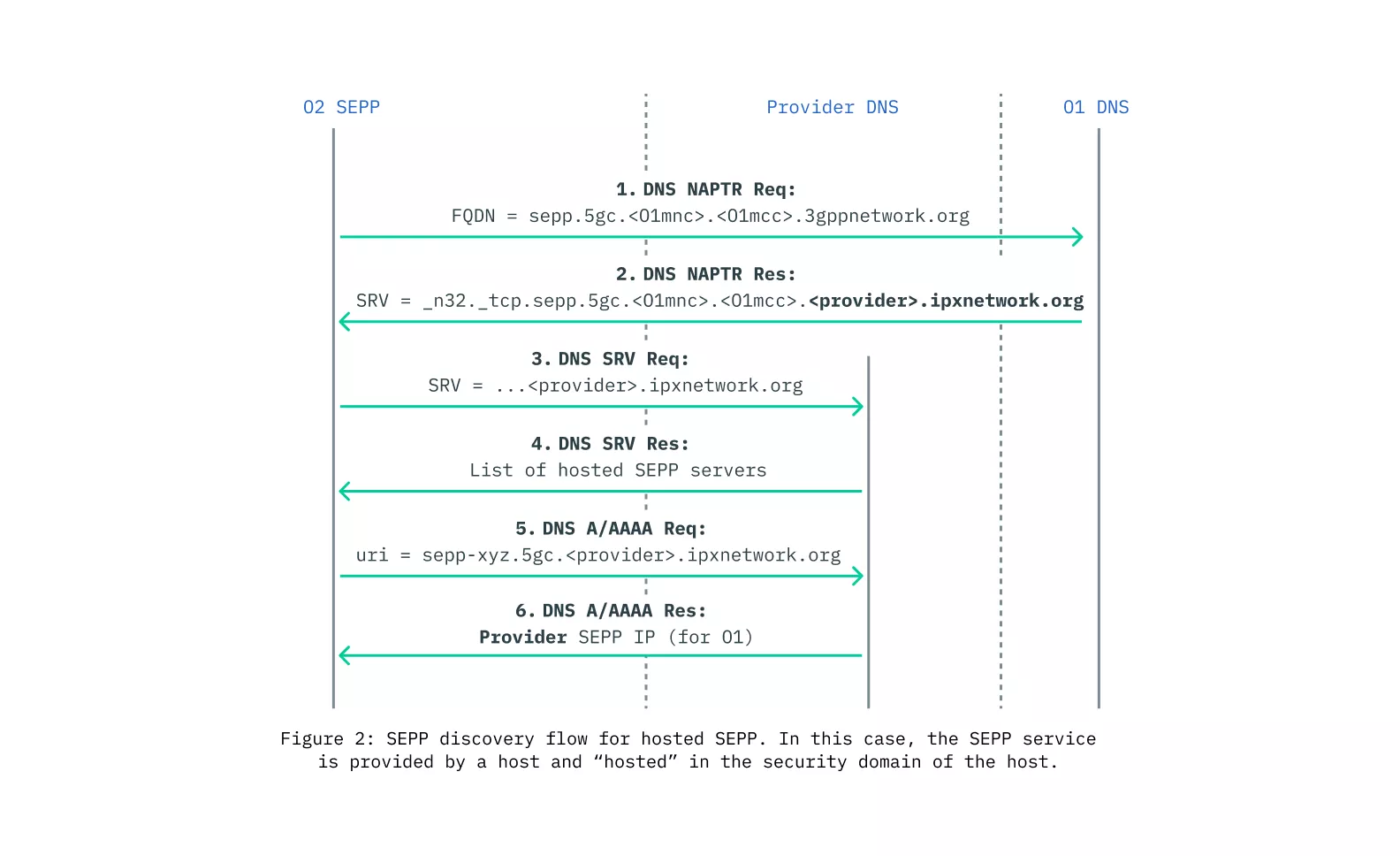
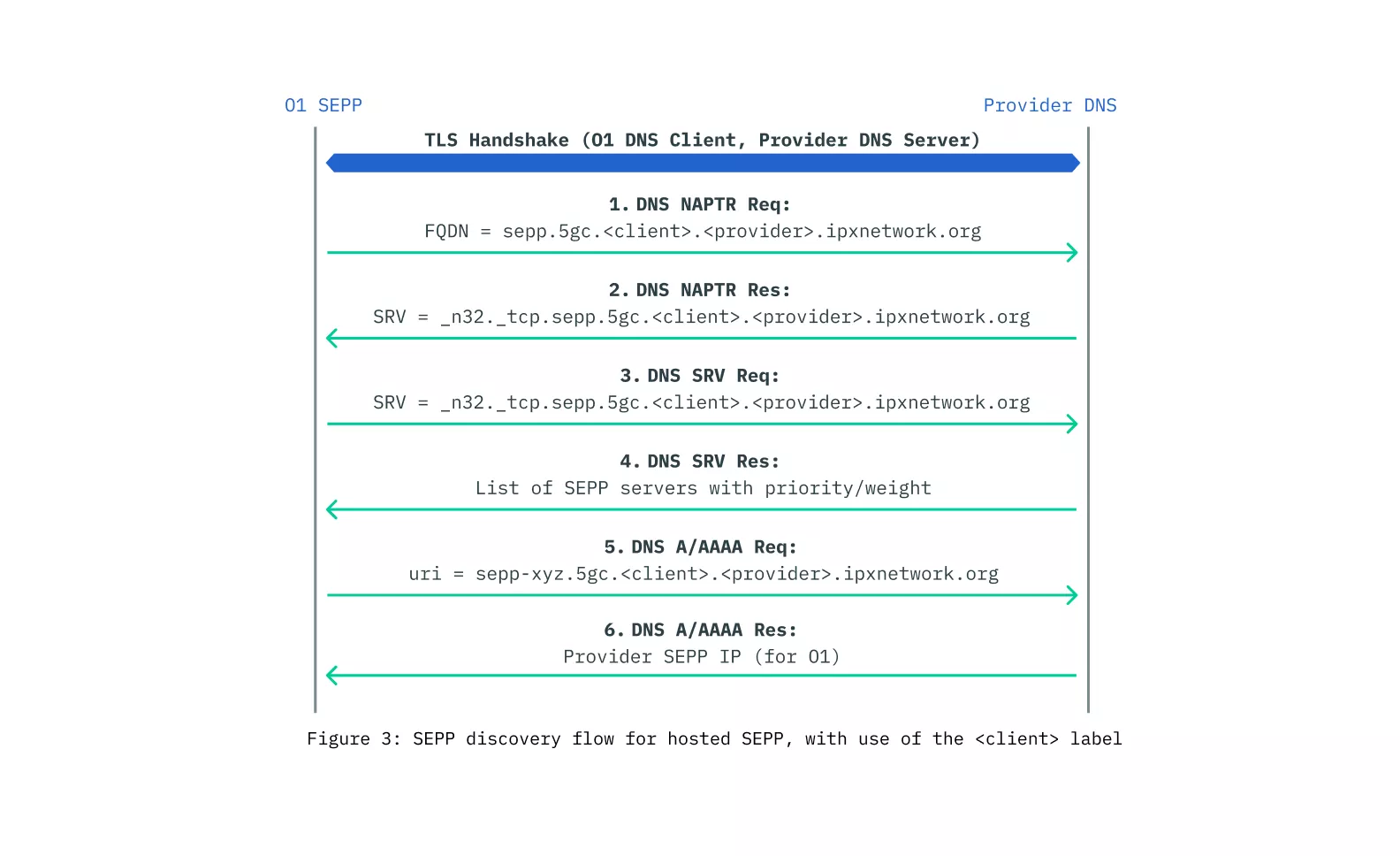
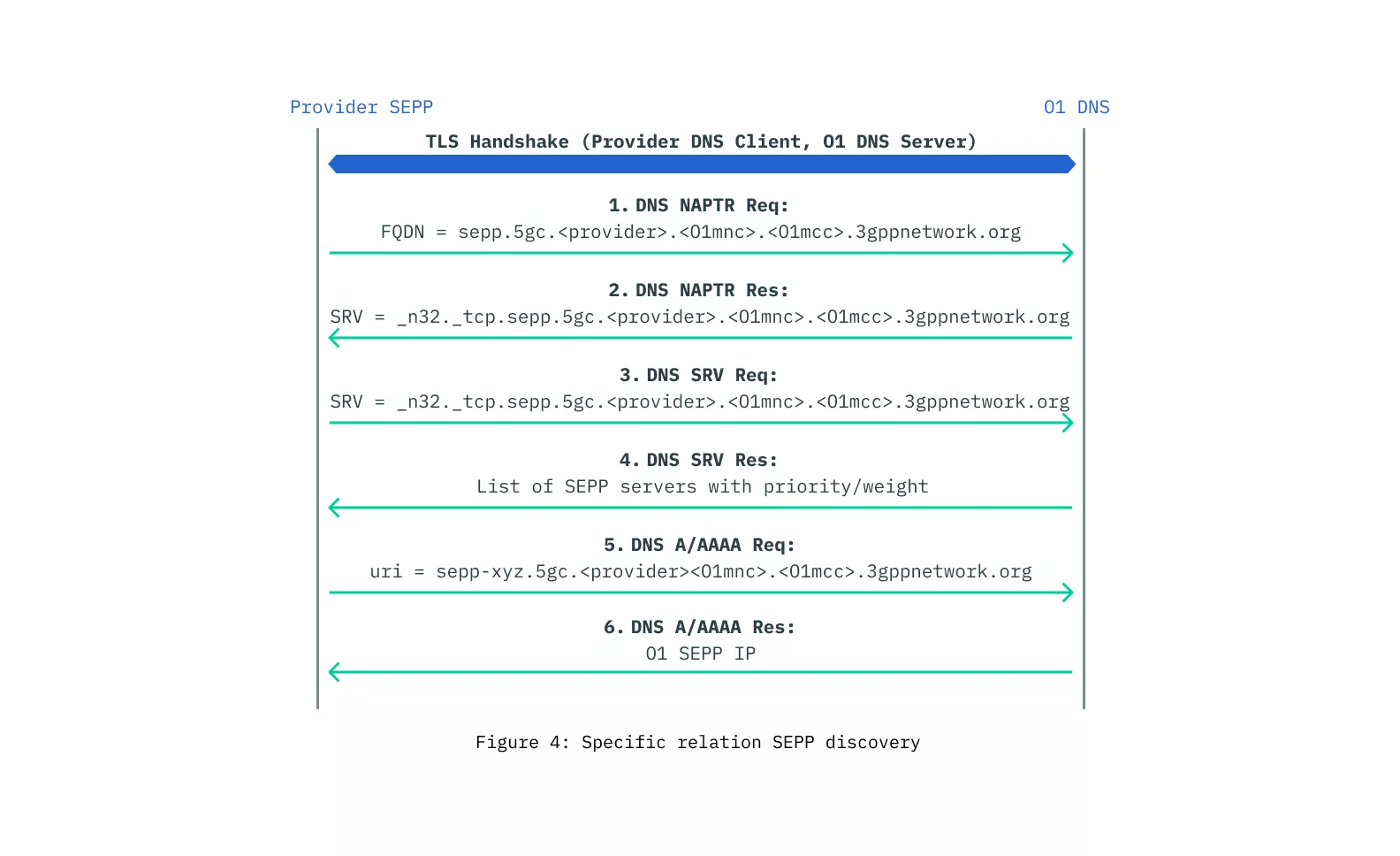
Introduction
As has been previously established, within the roaming ecosystem mobile operators often outsource various services to third parties, such as an IPX carrier or VAS provider.
In the interest of business continuity, an architecture is required that recognizes the relationship between service providers, which cater to a collection of (international) roaming relations. The subsequent chapters describe this architecture in technical detail: the scenario where only one operator has outsourced services, the case where both operators have outsourced services, and the common aspects of both options. This is then followed by an exploration of the use of N32-c between SEPPs.